ad1
ad2
Sunday, September 8, 2013
Monday, June 3, 2013
So you want your site listed in search engines, huh?
Once you've built your site, the next step is to get visitors to it.
Search engine rankings is a world of myths, out-of-date information, and big money. Chances are, if you done some research on this subject, you've found companies offering to submit your site to 1,000 search engines, 10,000 search engines, 100,000 search engines, and so on. Before we start, let's get this straight. There are around 10 search engines that matter. Their names are household names like Google, MSN, Yahoo, etc. You want to get listed with them, because they take 98.5% of the web searches (according to a Yahoo Finance Article).
So how do search engines work?
The truth of the matter is that no-one knows exactly. Most of what we know about Search Engine Optimization is derived from our own experiences, so different people will have different advice. Here's a basic overview of the common things that search engines like:
Got links?
Most search engines today (the ones that matter anyway) work as spiders, crawling links on the internet. In other words, they read web pages, looking for links to other web pages. The more links they find to a web page the more important that page must be. There is often no need to submit your site to them if other people link to your site, because the spiders will follow them to you. If you don't have other folks linking to your site, then submitting to the major search engines is still a good way to get the spiders started.
There are two types of links. Inbound and outbound. Inbound links are from another site to you, and act like 'votes' for your site. Outbound links are from you to someone else, and act like votes for someone else - you don't feel any benefit from it. If you have too many outbound links it might even negatively affect your ranking. So what you really want is for hundreds of people to voluntarily link to you. Depending on who you are and what your site contains, that probably won't happen, so you're going to have to arrange to make it happen!
Many people will be prepared to exchange links - they link to you in exchange for a link back. This is a good way to get your sites name out there, but ultimately you want one way links to you.
Directories are also a good way to get links to your site. Some charge, but there are many free ones around. The Open Directory Project (also known as the ODP or DMOZ) is one of the most important, if not the most important. Why? Simply because it's mirrored everywhere by other people in different countries, which gets you lots of backlinks from one submission. It also powers the Google Directory.
Forums are another option, but don't go round posting random posts like 'visit my wonderful new site at my.com'. This is usually considered very impolite--spamming... Some forums will allow you to link to your site in your signature. If you have useful content on your site you could link to it in a relevant discussion on a forum - e.g. if someone posts asking for information on a technique that you've used, you could post a link to that site as part of your answer.
Content?
The spider then reads the page, looking for keywords. You've probably heard a lot about putting keywords into your meta tags to get search engines to list you. You don't need meta-tags to get listed with the main search engines. You need content on your page. If you do use meta-tags then you need to make sure they really match your content - otherwise search engines might get the idea that you're trying to cheat.
The best way to get people to link to your site is to provide useful content. Articles for instance, like the one you're reading now! Chances are you got to this site either through one of the 209,000 links to HTML Goodies (at the time of writing), or through a search engine which followed those links.
Are you sure you've got content?
I know you're giving me funny looks through the screen, but this is important. You see, search engines don't see your site like Internet Explorer does. They see text. So you need to check your website can be read properly by search engines.
Things to watch out for include:
Javascript: You might have the most wonderful JavaScript powered menu in the world, but search engines don't usually read JavaScript. So make sure your menu is useable without it.
Images: there is a property for images called 'alternate text'. You see it used like this: <img src="somefile.gif" alt="some file or other"> Make sure you use it - it's all the search engine will see of your wonderful graphics, and that makes it important!
Clean code: If your site uses the first 500 lines just setting up your nested tables and rollover JavaScript effects, the important stuff gets pushed further down the page. Most search engines appear to stop reading your page after a certain point - usually a file size limit. If your site is listed, you can click the 'cached' button on most search engines to find out how much of your page it has read.
Structured code: Make sure your headings are marked up as headings (using <h1> etc) not a mix of bold and font tags. Heading tags are ranked as more important than bold tags, so use them and get your keywords into them. Don't forget you can use CSS to style the heading tags exactly as you want them, so you don't lose anything in terms of formatting.
Fancy fonts as images: Many people use images to get fancy fonts into their headings. If you're one of those people, you can markup your code as follows: <h1><img src="heading.jpg" alt="HTML Goodies.com - the place to learn HTML"></h1> (swap the h1 for the level of heading you need)
Title: There is a title tag buried in the head section of your page. Use it and make sure it's relevant - most search engines will use its content as the title of your listing.
Submit to Search Engines
As we've already mentioned, submitting isn't really necessary, but most search engines offer the option to submit your site. Here are the main URLs:
Google - powers AOL, Netscape etc.
Yahoo (Free Registration Required) - powers AltaVista, AllTheWeb etc.
MSN
Three Steps to Search Engine Optimization
So, to conclude, there are three main aspects to SEO.
Start with your code: you need to optimize your code to make it easy for the search engine to see what your page is about.
Next you need content: make your site worth linking to, and finally:
Get people linking to you!
Good luck, and hopefully I'll see you in the search engines!
Source : here
How to configure two Cisco Router together
Basic of Two Router LAB
Configuration of Router 1
Router>en
Router#conf t
Provide Host name to the router 1
Router(config)#hostname R1
Assign IP address to the R1 port
R1(config)#int fa0/0
R1(config-if)#ip add 10.1.1.1 255.0.0.0
R1(config-if)#no shut
R1(config)#int fa0/1
R1(config-if)#ip add 192.168.1.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#exit
R1(config)#exit
To save Configuration
R1#copy running-config startup-config
Building configuration...
[OK]
Router#conf t
Provide Host name to the router 1
Router(config)#hostname R1
Assign IP address to the R1 port
R1(config)#int fa0/0
R1(config-if)#ip add 10.1.1.1 255.0.0.0
R1(config-if)#no shut
R1(config)#int fa0/1
R1(config-if)#ip add 192.168.1.1 255.255.255.0
R1(config-if)#no shut
R1(config-if)#exit
R1(config)#exit
To save Configuration
R1#copy running-config startup-config
Building configuration...
[OK]
Configuration of Router 2
Router>en
Router#conf t
Provide Host name to the router 1
Router(config)#hostname R2
assign IP address to the R2 port
R2(config)#int fa0/0
R2(config-if)#ip add 10.1.1.2 255.0.0.0
R2(config-if)#no shut
R2(config-if)#int fa0/1
R2(config-if)#ip add 172.17.1.1 255.255.0.0
R2(config-if)#no shut
R2(config-if)#exit
R2(config)#exit
To save Configuration
R2#copy running-config startup-config
Building configuration...
[OK]
Router#conf t
Provide Host name to the router 1
Router(config)#hostname R2
assign IP address to the R2 port
R2(config)#int fa0/0
R2(config-if)#ip add 10.1.1.2 255.0.0.0
R2(config-if)#no shut
R2(config-if)#int fa0/1
R2(config-if)#ip add 172.17.1.1 255.255.0.0
R2(config-if)#no shut
R2(config-if)#exit
R2(config)#exit
To save Configuration
R2#copy running-config startup-config
Building configuration...
[OK]
How to Configure VLAN in Cisco switch
VLAN is Stand for Virtual LAN. It means device logically divided in to
different -2 LAN . Its improve security and reliability of your network.
Switch create logical broadcast domain to each VLAN.
switch1>en
switch1#conf t
switch2#vlan database
switch1(vlan)#vlan 10
VLAN 10 added:
Name: VLAN0010
switch1(vlan)#vlan 20
VLAN 20 added:
Name: VLAN0020
switch1(vlan)#exit
APPLY completed.
Exiting....
switch1#
switch1>en
switch1#conf t
switch1(config)#int vlan 10
switch1(config-if)#ip add 192.168.1.1 255.255.255.0
switch1(config-if)#no shut
switch1(config-if)#exit
switch1(config)#int vlan 20
switch1(config-if)#ip add 192.168.2.1 255.255.255.0
switch1(config-if)#no shut
switch1(config-if)#exit
switch1(config)#exit
switch1#conf t
switch1(config)#int f0/2
switch1(config-if)#switchport mode access
switch1(config-if)#switchport access vlan 10
VLAN Creation in Switch 1
switch1>en
switch1#conf t
switch2#vlan database
switch1(vlan)#vlan 10
VLAN 10 added:
Name: VLAN0010
switch1(vlan)#vlan 20
VLAN 20 added:
Name: VLAN0020
switch1(vlan)#exit
APPLY completed.
Exiting....
switch1#
Assign IP address to the VLAN
switch1>en
switch1#conf t
switch1(config)#int vlan 10
switch1(config-if)#ip add 192.168.1.1 255.255.255.0
switch1(config-if)#no shut
switch1(config-if)#exit
switch1(config)#int vlan 20
switch1(config-if)#ip add 192.168.2.1 255.255.255.0
switch1(config-if)#no shut
switch1(config-if)#exit
switch1(config)#exit
Assign Port to the VLAN
switch1#conf t
switch1(config)#int f0/2
switch1(config-if)#switchport mode access
switch1(config-if)#switchport access vlan 10
switch1(config-if)#int f0/3
switch1(config-if)#switchport mode access
switch1(config-if)#switchport access vlan 10
switch1(config-if)#int f0/4
switch1(config-if)#switchport mode access
switch1(config-if)#switchport access vlan 20
switch1(config-if)#int f0/5
switch1(config-if)#switchport access vlan 10
switch1(config-if)#int f0/4
switch1(config-if)#switchport mode access
switch1(config-if)#switchport access vlan 20
switch1(config-if)#int f0/5
switch1(config-if)#switchport mode access
switch1(config-if)#switchport access vlan 20
switch1#sh vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------
1 default active Fa0/1, Fa0/6, Fa0/7Fa0/8
Fa0/9, Fa0/10, Fa0/Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig1/1, Gig1/2
10 VLAN0010 active Fa0/2, Fa0/3
20 VLAN0020 active Fa0/4, Fa0/5
switch2#conf t
switch2#vlan database
switch2(vlan)#vlan 10
VLAN 10 added
Name: VLAN0010
switch2(vlan)#vlan 20
VLAN 20 added:
Name: VLAN0020
switch2(vlan)#exit
APPLY completed.
Exiting....
switch2#conf t
switch2(config)#int vlan 10
switch2(config-if)#ip add 192.168.1.1 255.255.255.0
switch2(config-if)#no shut
switch2(config-if)#exit
switch2(config)#int vlan 20
switch2(config-if)#ip add 192.168.2.1 255.255.255.0
switch2(config-if)#no shut
switch2(config-if)#exit
switch2(config)#int f0/2
switch1(config-if)#switchport mode access
switch2(config-if)#switchport access vlan 10
switch2(config-if)#int f0/3
switch1(config-if)#switchport mode access
switch2(config-if)#switchport access vlan 10
switch2(config-if)#int f0/4
switch1(config-if)#switchport mode access
switch2(config-if)#switchport access vlan 20
switch2(config-if)#int f0/5
switch1(config-if)#switchport mode access
switch2(config-if)#switchport access vlan 20
switch2(config-if)#exit
switch2#sh vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------
1 default active Fa0/1, Fa0/6, Fa0/7Fa0/8
Fa0/9, Fa0/10, Fa0/Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig1/1, Gig1/2
10 VLAN0010 active Fa0/2, Fa0/3
20 VLAN0020 active Fa0/4, Fa0/5
In this information port Fa0/2 and Fa0/3 are define for VLAN 10 , and Port Fa0/4 and Fa0/5 are define for VLAN 20
switch1(config-if)#switchport access vlan 20
Show VLAN INFORMATION
switch1#sh vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------
1 default active Fa0/1, Fa0/6, Fa0/7Fa0/8
Fa0/9, Fa0/10, Fa0/Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig1/1, Gig1/2
10 VLAN0010 active Fa0/2, Fa0/3
20 VLAN0020 active Fa0/4, Fa0/5
VLAN Creation in Switch 2
switch2>enswitch2#conf t
switch2#vlan database
switch2(vlan)#vlan 10
VLAN 10 added
Name: VLAN0010
switch2(vlan)#vlan 20
VLAN 20 added:
Name: VLAN0020
switch2(vlan)#exit
APPLY completed.
Exiting....
Assign IP address to the VLAN
switch2>enswitch2#conf t
switch2(config)#int vlan 10
switch2(config-if)#ip add 192.168.1.1 255.255.255.0
switch2(config-if)#no shut
switch2(config-if)#exit
switch2(config)#int vlan 20
switch2(config-if)#ip add 192.168.2.1 255.255.255.0
switch2(config-if)#no shut
switch2(config-if)#exit
Assign Switch Port to VLAN
switch2#conf tswitch2(config)#int f0/2
switch1(config-if)#switchport mode access
switch2(config-if)#switchport access vlan 10
switch2(config-if)#int f0/3
switch1(config-if)#switchport mode access
switch2(config-if)#switchport access vlan 10
switch2(config-if)#int f0/4
switch1(config-if)#switchport mode access
switch2(config-if)#switchport access vlan 20
switch2(config-if)#int f0/5
switch1(config-if)#switchport mode access
switch2(config-if)#switchport access vlan 20
switch2(config-if)#exit
Show VLAN information in switch 2
switch2#sh vlan
VLAN Name Status Ports
---- -------------------------------- --------- -------------------------
1 default active Fa0/1, Fa0/6, Fa0/7Fa0/8
Fa0/9, Fa0/10, Fa0/Fa0/12
Fa0/13, Fa0/14, Fa0/15, Fa0/16
Fa0/17, Fa0/18, Fa0/19, Fa0/20
Fa0/21, Fa0/22, Fa0/23, Fa0/24
Gig1/1, Gig1/2
10 VLAN0010 active Fa0/2, Fa0/3
20 VLAN0020 active Fa0/4, Fa0/5
How to Configure FTP Server In Windows 7
To Configure
FTP Server, FTP service should be install on Local Computer , And user
must be member of the Administrative Group on the local computer . With
the Help of FTP server we can share any file or folder with in a
network.
Follow these steps to Configure FTP Server .
1. Click on start Button , then Click on Control Panel, then Click on Program and Features
2. In Program and Feature window Click on Turn Windows Feature on or Off.
3. Expand Internet Information service Node .
4. Expand FTP server, then select FTP service Check-box, then click on Ok.
5. Now Go to the Control panel, then Click on Administrative tool.
5. Click on IIS manager, Click the Connection pane.
6. Right click on the Site, then Click on Add FTP sites.
7. In the Add FTP wizard , Write the name of FTP site and Select the Path of Folder which you want to share, then 8. Enter the Loopback address(127.0.0.1) in IP address Box, and Port 21. then click ok.
 |
8. Go to IIS and click on the created Sites , the Content of the site will be display.
How to Create Share Folder In Windows 7
1. Click on Start , then Click on My Computer, then Double-Click on Any Drive.
2. Right Click on Folder (ComNetworks) which is you want to Share, then Click on Properties.
3. Click on Sharing tab, then Click on Share...
4. Click on Drop-Down menu and select Everyone, Then Click on Share.
5. Click on Done To Complete Sharing.
2. Right Click on Folder (ComNetworks) which is you want to Share, then Click on Properties.
4. Click on Drop-Down menu and select Everyone, Then Click on Share.
5. Click on Done To Complete Sharing.
How to Prohibit Access to LAN Connection Properties in windows 7 via Group Policy
Suppose
that you have given Admin rights to the your then user change IP
address of network Connection , but and do not want to user can change
IP address of Network Connection then you can prohibit to user to access
network connection Properties .
Follow these steps to prohibit access to LAN Connection properties
1. Click on Start Button , then type gpedit.msc in Search box and press Enter.
2. Local Group Policy Editor window opened , Navigate User Configuration => Administrative template => Network Connection , then on the Right pane Double-Click on Prohibit access to properties of a LAN connection .
3. Click on Enable Radio button , then Apply and OK .
Like above setting also Have to Enable these Policy Listed below.......
- Prohibit access to properties of component of a LAN connection
- Prohibit TCP/IP advance Configuration .
- Enable windows 2000 network Connection setting for administrator .
How to share internet connection in windows 7
We can share internet connection between two computer Window 7. Two or
more two user can share internet connection simultaneously through
wireless connection or in a Local Network .
Share Internet connection step by step in windows 7
1. Click on start button, then click on Control panel, then click on Network and sharing center.
2. Click on Manage Wireless Networks on Network and sharing windows
2. Click on Manage Wireless Networks on Network and sharing windows
3. Now Network wireless connection opened, then Right Click the Connection which is want to share then click on Properties.
4. Now Properties box appear then click on Sharing Tab , .
Then Click Allow other Network user to connect through this computer internet connection .
5. Click the setting to ,then Check the service which you want to allow shared user. click on ok, then apply ,then Ok.
Thursday, May 30, 2013
USB Drive AutoRun.inf Tweaking
he autorun.inf file is the key to getting your USB drive (or
CD-ROM drive, for that matter) to perform certain actions automatically
and customize it’s look in My Computer. The purpose of this article is to shed some light on how this can be done.
Below this header is a list of different options. Each of these options is in the following format:
where
(Do not use
That is all there really is to understand about the structure of an autorun.inf file. On to doing some actual cool stuff with it!
You are not limited to .ico files. If, for example, you have an executable with a nice icon, you can specify it as the icon file. For example:
This is valid as long as DCoTopen.exe is available on the root of the USB drive.
Some files have more than one icon embedded in them. If this is the case, you can select which icon to use by specifing the index number after the file name. For example:
This will use the second icon in the iconlib.dll file.
Now, when you look at your USB drive in My Computer, it will say DCoT Drive by the drive letter.
The second option that we add is the message the user is prompted with. To set this, we use the
Once you have added this information, AutoPlay should look something like this:

The first thing that we need to do is create an action, give it a name, and a message. We do all of this using the
This will display Help! I’m Lost! in the context menu so that you can click on it. But, it doesn’t know what to do when you click on it. Tell the system by using
You can add as many of these line pairs as you want to make the context menu as custom as you want.
because lost is the name of the action that was specified in the earlier lines.
This will work for any file. This is the equivalent of using Start - Run… and then typing in a file name and clicking OK.
Download the zip file and extract the contents to the root of an empty USB drive. You can now edit the autorun.inf and get it to do different things. Have fun!
source: here
Autorun.inf Structure
The autorun.inf file is a simple text file that can be opened up in any text editor (e.g. notepad). It always starts with a section header of:[autorun]Below this header is a list of different options. Each of these options is in the following format:
option=valuewhere
option is the option that you want to set and value is the value that you are setting for that option. So, if you had an option foo and you wanted to be set to bar, then you would enter:foo=bar(Do not use
foo=bar in your autorun.inf file as it is only an example, not a real option setting.)That is all there really is to understand about the structure of an autorun.inf file. On to doing some actual cool stuff with it!
Setting a Custom Icon
To create a custom icon for your USB drive, use theicon option. Set it to the name of the icon file.Note: Since drive letters can change for USB drives, the file path is relative to the root of the drive. This means that if your USB drive is presently mounted on U: and your icon is located at U:\Icons\MyIcon.ico, then you would enter \Icons\MyIcon.ico for the value of this option.For example, if you had an icon on the root of the USB drive called coffeecup.ico and you wanted this to be the icon that showed up for the USB drive, you would enter:
icon=coffeecup.icoYou are not limited to .ico files. If, for example, you have an executable with a nice icon, you can specify it as the icon file. For example:
icon=DCoTopen.exeSome files have more than one icon embedded in them. If this is the case, you can select which icon to use by specifing the index number after the file name. For example:
icon=iconlib.dll,2This will use the second icon in the iconlib.dll file.
Naming Your USB Drive
If you would like your USB drive to display a specific name othr than the drive label created when it is formatted, use thelabel option. For example, if I wanted to call my drive DCoT Drive, I would add this to my autorun.inf file:label=DCoT DriveNow, when you look at your USB drive in My Computer, it will say DCoT Drive by the drive letter.
Setting AutoPlay Options
AutoPlay is a relatively new function of Windows XP. It allows you to set up what file is run when the USB drive is plugged into the computer and the message that you are prompted with. There are two options that work in conjunction with AutoPlay. The first isopen. It specifies the program that you can run automatically with AutoPlay. So, if we wanted to run a program called DCoTopen.exe, you would add the this to your autorun.inf file:open=DCoTopen.exeThe second option that we add is the message the user is prompted with. To set this, we use the
action option. If we want the message to say DCoT Open Program, add the following to autorun.inf:action=DCoT Open ProgramOnce you have added this information, AutoPlay should look something like this:

Adding Context Menu Items
There are certain basic options such as Open and Explore that are available when you right click on a USB drive. But, wouldn’t it be cool to add your own? You can using a couple of lines in the autorun.inf file.The first thing that we need to do is create an action, give it a name, and a message. We do all of this using the
shell\verb option. For example, let’s say that we would like to create an action called lost. It does not matter what the actin is called. It can be anything you want. We would also like to show the message Help! I’m Lost! in the context menu. We would simply add this line to autorun.inf:shell\lost=Help! I'm Lost!This will display Help! I’m Lost! in the context menu so that you can click on it. But, it doesn’t know what to do when you click on it. Tell the system by using
shell\verb\command option. In our example, we want to run the Lost.exe application. Adding this line will do the trick:shell\lost\command=Lost.exeYou can add as many of these line pairs as you want to make the context menu as custom as you want.
Changing Default Action
When you double click on your USB drive, by default it will open up the drive so that you can browse through the files. Often, it is advantageous to perform some other action when the user double clicks the USB drive icon. You do this with theshell option. If we wanted to run the Lost.exe program from the previous section automatically when we double clicked on the USB drive, we would add this line:shell=lostbecause lost is the name of the action that was specified in the earlier lines.
Viewing a File
If you wanted to view a file on your USB drive in the default application instead of running a program on the drive, you can substitute theopen option for the shellexecute option. For example, if you wanted to open up a website called, oh, I don’t know, say http://www.DailyCupOfTech.com in the default web browser, you could user the following:shellexecute=http://www.DailyCupOfTech.comThis will work for any file. This is the equivalent of using Start - Run… and then typing in a file name and clicking OK.
School’s Out, Time To Play!
That is about all there is to customizing the autorun.ing file. Now that you know what you are doing, it’s time to start playing! I have created the Autorun Dabbler’s Toolkit that you can play with.Download the zip file and extract the contents to the root of an empty USB drive. You can now edit the autorun.inf and get it to do different things. Have fun!
source: here
How to make money online with LINKBUCKS using TPT (Traffic W) ?
Linkbucks is an advertising network that allows you to make money
from sharing your links by shortening them and spreading them all over
the internet.

What are the requirements?
- basically all you need is internet access and you also need to be active online in order for you to make any cash
- you also need to have a way to get the money. you can use paypal or other methods that they have and be sure that you can get paid from any country.
You dont need
- to have a website
- to pay anything
- to write any code
Possible Tactics-(if you wish)
- you could start a blog and share links to your blog articles, you need to write about interesting stuff
- you could start a forum where people can discuss about something
- start a facebook group and get lots of visitors from that group
- put videos on youtube and put your links in the description
Getting started
- all you have to do is sign up for FREE here
- fill your details and that's it. after confirming your email address you can click the create links tab and start shortening links.
- start spreading your links on the internet i write about how to do this in my other posts so look around
You should know that the rate of making money will be slow
especially if the people clicking your links are are not from top
countries (UK, USA etc) so try to get visitors from these countries to
increase your earnings. That's all you need.
What is Traffic W?
Traffic W its a Traffic Exchange, just in a bot made off some Chinse people something.
Over 15 Million people use it everyday to earn big traffic to their sites.
You just need to run it and submit your sites you want Traffic too.
People also sell traffic from them to earn them som big cash everyday! Aslo hard used to exploit sites like& Linkbucks…
with Traffic W can you only add 4-6 links! Thats just bad for Traffic selling.
Over 15 Million people use it everyday to earn big traffic to their sites.
You just need to run it and submit your sites you want Traffic too.
People also sell traffic from them to earn them som big cash everyday! Aslo hard used to exploit sites like& Linkbucks…
with Traffic W can you only add 4-6 links! Thats just bad for Traffic selling.
How to use Traffic W with Linkbucks ?
- Login
- create links
- Paste your link in
- select clean all ages or 18+
- then select intermission ads these are the higer paying ads the ones that ask you to skip ad after a short time.
- then select what mini url you want to use there are like 15 to choose from any will do.
- then click create link and your done a short link will be generated and you can use that link and each time a person clicks it you will make money.
Second : Download the software (Traffic W)
How to use the software
This is just a brief discussion/ tutorial .
Whats the use of this bot?
- You use this to make other people click on ads ( making money online )
- You use this to get more traffic to your website
- you can use this in some website that has PTP link.
1. Open the program.
This is just a brief discussion/ tutorial .
Whats the use of this bot?
- You use this to make other people click on ads ( making money online )
- You use this to get more traffic to your website
- you can use this in some website that has PTP link.
1. Open the program.
2. You'll see a button at the botton part of the software, you need to click on it
.
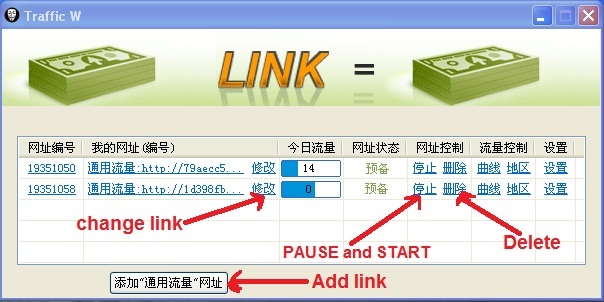
3. You'll see a box that will pop-up. You need to put your URL link there, in the box with (http://)
4. After you put your URL link there, you can now click the "ADD Link" button of the pop up box to be able to start the bot running.
5. You can see beside your link that there is a loading icon (that's the number of views you'll accumulate, using the bot)
6. In line with your URL link, you'll see some chinese button.I will show you the important ones
Note: The number of your link depends on the speed of the internet you have ( next pop-up box tell you that you can't add other links ).
You don't need to use proxy or anything. You just need your link, and let it run.
Enjoy!
Enjoy!
Payment proof:
What is virus ?
In computers, a virus is a program or programming code that
replicates by being copied or initiating its copying to another program,
computer boot sector or document. Viruses can be transmitted as
attachments to an e-mail note or in a downloaded file, or be present on
a diskette or CD. The immediate source of the e-mail note, downloaded
file, or diskette you've received is usually unaware that it contains a
virus. Some viruses wreak their effect as soon as their code is
executed; other viruses lie dormant until circumstances cause their code
to be executed by the computer. Some viruses are benign or playful in
intent and effect ("Happy Birthday, Ludwig!") and some can be quite
harmful, erasing data or causing your hard disk to require reformatting.
A virus that replicates itself by resending itself as an e-mail
attachment or as part of a network message is known as a worm.
Generally, there are three main classes of viruses:
File infectors.
Some file infector viruses attach themselves to program files, usually
selected .COM or .EXE files. Some can infect any program for which
execution is requested, including .SYS, .OVL, .PRG, and .MNU files. When
the program is loaded, the virus is loaded as well. Other file
infector viruses arrive as wholly-contained programs or scripts sent as
an attachment to an e-mail note.
System or boot-record infectors. These viruses infect executable code found in certain system areas on a disk. They attach to the DOS boot sector
on diskettes or the Master Boot Record on hard disks. A typical
scenario (familiar to the author) is to receive a diskette from an
innocent source that contains a boot disk virus. When your operating
system is running, files on the diskette can be read without triggering
the boot disk virus. However, if you leave the diskette in the drive,
and then turn the computer off or reload the operating system, the
computer will look first in your A drive, find the diskette with its
boot disk virus, load it, and make it temporarily impossible to use your
hard disk. (Allow several days for recovery.) This is why you should
make sure you have a bootable floppy.
Macro viruses.
These are among the most common viruses, and they tend to do the least
damage. Macro viruses infect your Microsoft Word application and
typically insert unwanted words or phrases.
The best protection
against a virus is to know the origin of each program or file you load
into your computer or open from your e-mail program. Since this is
difficult, you can buy anti-virus software
that can screen e-mail attachments and also check all of your files
periodically and remove any viruses that are found. From time to time,
you may get an e-mail message warning of a new virus. Unless the
warning is from a source you recognize, chances are good that the
warning is a virus hoax.
The computer virus, of course, gets its name from the biological virus. The word itself comes from a Latin word meaning slimy liquid or poison.
What is hacking?
J.H. Hamlyn-Harris, Swinburne University of Technology
Friday, 05 April 2013
Friday, 05 April 2013
Last week, we woke to news that the largest cyber attack ever was
underway in Europe, with reports of global internet speeds falling as a
result of an assault on the anti-spamming company Spamhaus.
In recent weeks, the Reserve Bank of Australia has been the target of
a cyber attack, as have South Korean banks and broadcasters and BBC
Twitter accounts.
The above stories were all reported as "hacking" - a blanket term
readily used to encompass a whole range of attacks, from crashing a
server to more sophisticated infiltration, such as stealing passwords.
But, generally, news stories don't discriminate.
So what are hackers and their methods really like? What follows is
something of a glossary, to cut out (or at least bookmark) and keep.
Types of hackersPhreakers:
Perhaps the oldest type of computer hackers, Phreakers discover how
telephone systems work and use their knowledge to make free phone calls.
In the past, phone phreakers used what we now think of as hacking
techniques to access mainframe computers and programmable telephone
switches to obtain information, alter records or evade capture.
Famous (and now retired) phreakers include Kevin Mitnick, Kevin Poulsen and Apple founders Steve Jobs and Steve Wozniak.
Crackers: These guys bypass (crack) security
controls on proprietary software, DVDs, computer games and Digital
Rights Management (DRM)-protected media.
Crackers trade, share and publish game "cracks", patches, serial
numbers and keygens (activation key generators). They also embed malware
in their cracks and patches forming Trojans to deter outsiders (mostly
"script kiddies"; see below) from using their code.
Unsuspecting people who use their cracks more often than not find
themselves infected with worms and viruses (explained below). Such
infections often bypass anti-virus tools and firewalls, and are probably
responsible for most of the malware on teenagers' home computers.
Black Hat Hackers: These are crackers who actively
develop malware and intrusion techniques and tools for evil purposes,
Black Hats are motivated by profit.
Criminal organisations, foreign governments and spy agencies will pay
handsomely for the latest zero-day (not publicly known) exploit.
Journalist Brian Krebs recently reported a bidding war for a Java exploit valued at more than US$5,000.
White Hat Hackers: These are the good guys. White Hats, also known as "ethical hackers" and "pen-testers", are security researchers.
They test systems (often using the same tools as Black Hats, but
within the law) by conducting penetration testing and security audits as
a service for businesses and organisations that don't want to be
hacked.
White Hats report on any vulnerabilities found and what needs to be
done to fix them. Both the US and Australian governments have set up
competitions to encourage school and university students to take up
(White Hat) hacking as a career. (My Swinburne team competed in the
pilot version of Australia's Cyber Challenge in 2012 and scored higher
than all other Victorian universities.)
Grey Hat Hackers: Grey Hats generally work within
the law but may publish vulnerabilities and exploits or sell exploits to
unknown buyers without asking too many questions.
They may also report vulnerabilities to software vendors anonymously
to avoid prosecution. Unfortunately some vendors object to having their
defective code discovered and discourage security research on their
products.
Script kiddies: Also known as "skiddies", these are a
growing number of amateur Black Hats who cannot develop their own code
but can adapt other people's exploits and use hack tools to attack
organisations and each other.
Script kiddies find the term offensive and have been known to launch
cyber-attacks against people who have denigrated them or their skills.
It is likely that many of the "hackers" associated with online protest group Anonymous are script kiddies.
Cyber-troops, cyber-soldiers: These are
state-sponsored military personnel trained in hacking techniques who use
malware and hacking techniques to spy, gather intelligence, steal
intellectual property and disrupt enemy systems.
Spammers and Phishers: Spammers use programs -
spambots - to automatically send email, SMSs, instant messages and
tweets to potential buyers of their products.
Phishers use the same technologies (and fake "pharming" sites) to
entice victims to click on links (and type in user-names and passwords)
and download and install malware. The book Spam Kings recounts the early
history of many spammers.
Types of hacks
Now that we know who the bad guys are, let's consider what they do and how their actions are likely to affect people.
Script injection (SQL, JavaScript) attacks: Most
websites are connected to databases. With Structured Query Language
(SQL) injection, attackers run their own code on these databases,
allowing them to change records, delete data and extract private
information such as credit card numbers, passwords or password hashes.
JavaScript injection happens through publicly-writable web sites such
as Facebook, Twitter and sites with forums and discussion boards. If
not properly filtered, an attacker can upload script that extracts
private information from people visiting the site.
Scripts can bypass firewalls to extract user credentials, track user
activities, install malware and even turn on the web camera and
microphone. The simplest way to prevent such attacks is to turn off
scripting (in your browser).
The Firefox NoScript plug-in is an easy way to do this.
Password cracking: Simply put, if an attacker can
guess your password, he or she can take over your computer. Most
computer users are overwhelmed by the number of account names and
passwords they have to remember, so they tend to re-use them.
An attacker can use SQL injection to recover passwords or password
hashes from a poorly-secured website, and then try the same user-names
and passwords to log into high-value sites such as bank accounts.
Websites and email systems that restrict password length are the easiest to attack.
Brute force attacks: These use automated tools to guess the password or re-create the password hash.
The most effective ways of preventing this is to (a) use long passwords, and (b) use different passwords.
DoS/DDoS: (Distributed) Denial of service attacks are generally
launched against organisations, whose servers are flooded with "broken"
network communications that cause the servers to slow down or even
crash.
Companies that rely on online trading will lose a lot of money (and
reputation) if this happens, and will often pay the attackers to call
off the attack.
Viruses, worms and trojans: These are infection
carriers used to distribute malware. Viruses travel by thumb drives,
worms travel through the internet, and Trojans are downloaded by
unsuspecting users.
Anti-virus software will stop most of this, but not the latest (or zero-day) malware attacks.
Crimeware, hijackers and ransomware: Black Hat
hacking has matured into an industry. Hackers can purchase crimeware
packs for a few thousand dollars and start up a business distributing
malware, accepting payments and laundering money.
Hijackers take over your web browser and redirect you to advertising
sites. Ransomware infects your computer and prompts you to call a
toll-free number, where you can pay to have your computer remotely
"disinfected".
Man-in-the-browser malware, such as Zeus, can intercept your online
banking sessions in your browser and phone, draining your account by
sending money to the attackers.
Bots and bot-nets: Bots emulate human users. Once a bot has infected
your computer, you are "owned". Your computer (now a zombie) is remotely
controlled by a bot herder who can use it and hundreds of thousands of
other zombies to launch DDoS attacks, crack passwords, send spam and
host illegal content.
Protect yourself
We can only minimise the risks,
but the risks are well understood. Turn off scripting, maintain your
anti-virus, don't read unsolicited emails, use long passwords, use
different passwords, don't download programs you didn't go looking for,
be sceptical ... and finally: learn about computer security (to find out
what else you can do).
There's no need to be paranoid. Just be careful. White Hat hackers
are there to help by exposing the risks and testing the systems. Trust
them. They're the good guys.
James H. Hamlyn-Harris does not work for,
consult to, own shares in or receive funding from any company or
organisation that would benefit from this article, and has no relevant
affiliations.
Subscribe to:
Posts (Atom)


















